Tag: Cybersecurity
Betechit News Analysis : The Latest Trends In Tech Innovations
In an era where Betechit News holds the key to understanding today's rapidly evolving landscape, technology enthusiasts find themselves at the forefront of tech...
Safeguarding Your Digital Footprint: Insights and Strategies
In today’s digital age, our lives are more connected to the internet than ever before. From social media accounts to online banking, the traces...
FBI Investigating Iran’s Hack of Trump Campaign: Latest Updates and Analysis
The FBI has confirmed that it is currently investigating cyber hacking attempts by Iran against the 2024 presidential campaign of former President Trump. This...
FBI Enlists Israeli Firm to Decrypt Gunman’s Messages in Trump Assassination...
The FBI has sought the assistance of the Israeli tech company Cellebrite to aid in the investigation of Thomas Matthew Crooks, the 20-year-old man...
Family of Fallen Firefighter Corey Comperatore Addresses Facebook Impersonation Scandal
Scammers on social media are pretending to be the family of Corey Comperatore, a firefighter who tragically lost his life at a rally in...
Investigation Reveals FBI Accesses Phone in Trump Assassination Plot
The FBI recently announced that they were able to access the phone of Thomas Matthew Crooks, the individual who attempted to assassinate former President...
Cyber-attack Disrupts Car Dealers in US and Canada for Third Day
A cyber incident at a major retail software provider for automobile dealers has caused disruptions for the third day in a row, affecting car...
Protect Your Data: How to Prevent High-Risk Vulnerabilities for Chrome Users
CERT-In has recently issued a warning about critical vulnerabilities found in Google Chrome for desktop users. These vulnerabilities are considered high-risk and users are...
Top 23 In-Demand Tech Skills for Hiring Success
Companies across industries are constantly in need of tech professionals to help with various tasks such as preventing cyberattacks and developing new "smart" applications....
PHP Injection Vulnerability CVE-2024-4577 in Windows Server
A critical security flaw affecting PHP servers on Windows operating systems has been identified as CVE-2024-4577. This vulnerability allows for remote code execution and...
Data Breach Alert: Truist Bank Notifies Clients of Compromised Financial Account...
Truist Bank recently made headlines after filing a notice of data breach with the Attorney General of Massachusetts on June 11, 2024. The bank...
CyberArk Software (CYBR) Stock Surges with High Trading Volume
CyberArk Software Ltd. (NASDAQ: CYBR) experienced a surge in stock price accompanied by high trading volume on Friday. The trading volume reached 264,623 shares,...
Prevent Remote Workers from Getting Caught with ‘Mouse-Mover’ Technology
Last month, Wells Fargo reportedly fired over a dozen employees for using devices or apps to fake productivity on their computers. These employees were...
The main target and focus of the article is to uncover...
It has been almost a decade since the Ashley Madison scandal, where hackers leaked personal data from the dating site known for facilitating extramarital...
Alexis Ren Discusses Technology and Agoraphobia in ‘Latency’SEO Alexis...
Alexis Ren, a well-known social media influencer and model, recently opened up about her views on technology and agoraphobia in her latest project, 'Latency'....
GPT-4 autonomously hacks zero-day security flaws with 53% success rate
GPT-4, an advanced language model, has been making waves in the cybersecurity world. Initially known for autonomously hacking one-day vulnerabilities with an impressive success...
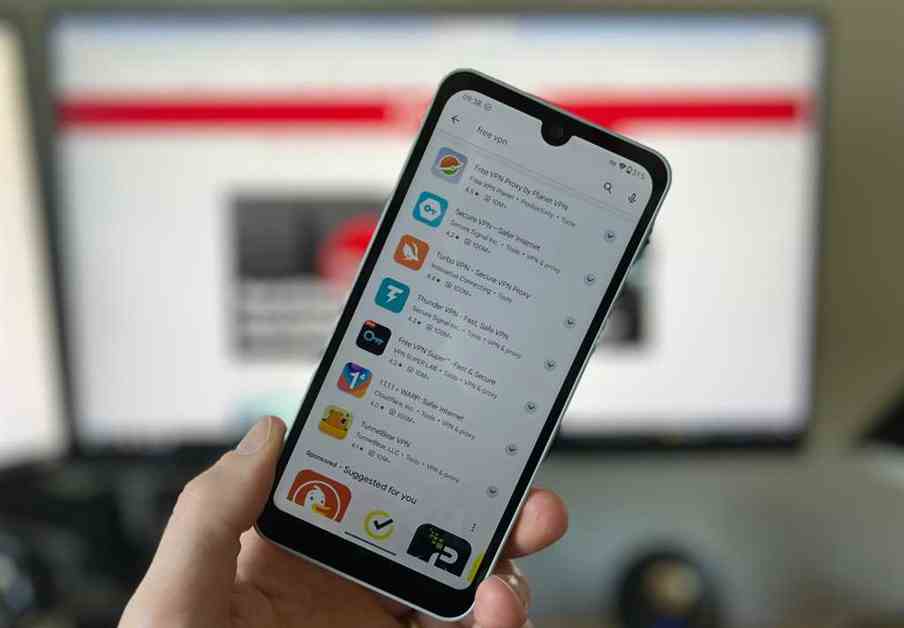
Privacy issues with top free Android VPNs puts 2.5 billion users...
Privacy Concerns Arise as Top Free Android VPNs Compromise 2.5 Billion UsersIn a recent study conducted by Top10VPN, it has been revealed that a...
Trends releases study on threats of AI in information warfare
Trends Research Warns About Risks of AI in Information WarfareTrends Research and Advisory recently published a study highlighting the dangers of using artificial intelligence...
Critical Apache Log4j2 flaw still threatens global finance – Security Affairs
Global Finance Industry at Risk Due to Critical Apache Log4j2 VulnerabilityThe cybersecurity world is on high alert as a critical vulnerability in the Apache...
Generative AI for Security: Harnessing Amazon Bedrock for Customer Impact –...
Harnessing GenAI for Cybersecurity: Revolutionizing Security PracticesCybercriminals are utilizing advanced tools like generative AI (GenAI) to launch attacks more efficiently, posing a significant threat...
Security Bite: Apple refused to pay bounty to Kaspersky for uncovering...
Apple’s Refusal to Pay Security Bounty to Kaspersky Raises ConcernsKaspersky, a well-known cybersecurity firm, gained attention last year for uncovering an attack chain involving...